Alteryx Designer Desktop Discussions
Find answers, ask questions, and share expertise about Alteryx Designer Desktop and Intelligence Suite.- Community
- :
- Community
- :
- Participate
- :
- Discussions
- :
- Designer Desktop
- :
- Re: API Download Tool Error transferring data: SSL...
API Download Tool Error transferring data: SSL connect error
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify Moderator
Hello,
I'm getting Error transferring data: SSL connect error when using the Download tool to call to an API. I just upgraded to 2022.1. I reinstalled 2021.4 and it worked on that version. I've also verified the keys/client Id work on Postman. Any ideas what changed in the upgrade?
Thanks.
- Labels:
-
Download
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify Moderator
@Paul_Holden Based on the document below, 2022.1 uses OpenSSL 3.0. I'm not able to determine the version used in 2020.4.
Alteryx’s Response to CVE-2022-3602 and CVE-2022-3786 (Spooky SSL)
Sr CSE
Alteryx
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify Moderator
@EdP thanks. I'm still thinking that this is an issue with our Netscaler but I'm struggling to find the key that opens the lock with our networking team.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify Moderator
We have done some more work on this and it seems almost certain that the issue is that the Netscaler Load-balancer that sits in front of the application servers is set to deny all SSL renegotiation.
I have asked if this can be changed to deny only INSECURE renegotiation which I believe might resolve the issue.
However my Netsec team have come back and asked why Alteryx uses SSL renegotiation at all. They are saying that it is fundamentally insecure (even the "secure" version) to the extent that it has been removed from TLS 1.3
At this point they are refusing to change the NS-LB configuration without further justification and/or confirmation that Alteryx cannot be re-configured to not use renegotiation.
They are also asking why this issue has only just come up when TLS renegotiation issues and fixes are now many years old, e.g. CVE-2009-3555 which is 2009
Is there a fundamental flaw in OpenSSL that means that no renegotiation is a vulnerable configuration? If so I'm struggling to find a document that I can point to which is newer than the comments on CVE-2009-3555 and RFC5746 which are sufficiently old that I cannot explain to my Netsec team why the 2020 version of Alteryx did not suffer this same issue.
Anyone have anything that I can go back with on this. Comment by @GloriousWater that secure should be better that insecure is unfortunately not carrying much weight with them as they are saying that any is worse than none?
Regards,
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify Moderator
Hi @Paul_Holden
My comment about deny only insecure was more safe was just parroting one of our guys from the IT dept. I believe it was just a quick thought train, that a double handshake should be better than one, but from a quick google this opens a vulnerability for DDOSing the server.
I believe you should be able to use the python tool to query your server instead of the download tool as the python tool should (i believe it should work but i have not tested it) allow you to disable the renegotiation as you essentially write the code for your request rather than use the UI of the download tool that is a bit more hard coded.
I hope you find a solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify Moderator
Thanks for the comments. Right now I'm trying to get some more information from the Alteryx devs as to why they activated renegotiation in the latest version. Whether that was a mistake or whether secure reneg is actually better than no reneg in the specific circumstances of the download tool.
If it is then I can get our Netsec team to allow it on the endpoint(s) that Alteryx is hitting.
If it isn't then I'm hoping we can get a fix from Alteryx to allow us to switch off reneg for the download tool.
The python tool is fine if you have python dev resource available. Unfortunately in this case, and I can't believe we are alone in this, the USP for Alteryx was that it was a "no code" solution and that was the basis on which it was chosen. Turning around to the business and telling them they now need developer time to make the workflow functional again is not a good look.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify Moderator
Server 2022.3 has been released and includes a configuration file to provide a means to adjust security checks performed by the Download Tool on a site-by-site basis. This replaces any previous workarounds.
Please see: https://help.alteryx.com/20223/designer/peer-validation-allow-list
Sr CSE
Alteryx
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify Moderator
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify Moderator
This worked for us after upgrading to 2022.3.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify Moderator
I need to see if I can agree a maintenance window for another upgrade to Alteryx.
I'm still not convinced that this is going to resolve the issue for us since the problem is NOT that the remote system does not support secure renegotiation it is that the remote system does not support renegotiation at all. So far all fixes supplied by the Alteryx devs have only tried to address the legacy vs secure renegotiation unfortunately.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify Moderator
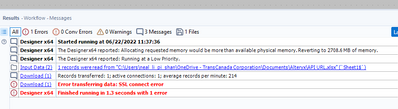
I can see the TLS Peer validation bypass in my results window but i am still receiving the SSL connect error
-
AAH
1 -
AAH Welcome
2 -
Academy
25 -
ADAPT
82 -
Add column
1 -
Administration
20 -
Adobe
179 -
Advanced Analytics
1 -
Advent of Code
5 -
Alias Manager
70 -
Alteryx
1 -
Alteryx 2020.1
3 -
Alteryx Academy
3 -
Alteryx Analytics
1 -
Alteryx Analytics Hub
2 -
Alteryx Community Introduction - MSA student at CSUF
1 -
Alteryx Connect
1 -
Alteryx Designer
44 -
Alteryx Engine
1 -
Alteryx Gallery
1 -
Alteryx Hub
1 -
alteryx open source
1 -
Alteryx Post response
1 -
Alteryx Practice
145 -
Alteryx team
1 -
Alteryx Tools
1 -
AlteryxForGood
1 -
Amazon s3
139 -
AMP Engine
194 -
ANALYSTE INNOVATEUR
1 -
Analytic App Support
1 -
Analytic Apps
17 -
Analytic Apps ACT
1 -
Analytics
2 -
Analyzer
17 -
Announcement
5 -
API
1,061 -
App
1 -
App Builder
49 -
Append Fields
1 -
Apps
1,174 -
Archiving process
1 -
ARIMA
1 -
Assigning metadata to CSV
1 -
Authentication
4 -
Automatic Update
1 -
Automating
3 -
Banking
1 -
Base64Encoding
1 -
Basic Table Reporting
1 -
Batch Macro
1,297 -
Beginner
1 -
Behavior Analysis
221 -
Best Practices
2,453 -
BI + Analytics + Data Science
1 -
Book Worm
2 -
Bug
633 -
Bugs & Issues
2 -
Calgary
59 -
CASS
48 -
Cat Person
1 -
Category Documentation
1 -
Category Input Output
2 -
Certification
4 -
Chained App
239 -
Challenge
7 -
Charting
1 -
Clients
3 -
Clustering
1 -
Common Use Cases
3,456 -
Communications
1 -
Community
198 -
Computer Vision
49 -
Concatenate
1 -
Conditional Column
1 -
Conditional statement
1 -
CONNECT AND SOLVE
1 -
Connecting
6 -
Connectors
1,211 -
Content Management
8 -
Contest
6 -
Conversation Starter
17 -
copy
1 -
COVID-19
4 -
Create a new spreadsheet by using exising data set
1 -
Credential Management
3 -
Curious*Little
1 -
Custom Formula Function
1 -
Custom Tools
1,753 -
Dash Board Creation
1 -
Data Analyse
1 -
Data Analysis
2 -
Data Analytics
1 -
Data Challenge
87 -
Data Cleansing
4 -
Data Connection
1 -
Data Investigation
3,128 -
Data Load
1 -
Data Science
39 -
Database Connection
1,931 -
Database Connections
5 -
Datasets
4,669 -
Date
3 -
Date and Time
3 -
date format
2 -
Date selection
2 -
Date Time
2,933 -
Dateformat
1 -
dates
1 -
datetimeparse
2 -
Defect
2 -
Demographic Analysis
173 -
Designer
1 -
Designer Cloud
508 -
Designer Integration
60 -
Developer
3,723 -
Developer Tools
3,012 -
Discussion
2 -
Documentation
461 -
Dog Person
4 -
Download
920 -
Duplicates rows
1 -
Duplicating rows
1 -
Dynamic
1 -
Dynamic Input
1 -
Dynamic Name
1 -
Dynamic Processing
2,595 -
dynamic replace
1 -
dynamically create tables for input files
1 -
Dynamically select column from excel
1 -
Email
776 -
Email Notification
1 -
Email Tool
2 -
Embed
1 -
embedded
1 -
Engine
130 -
Enhancement
3 -
Enhancements
2 -
Error Message
2,009 -
Error Messages
6 -
ETS
1 -
Events
181 -
Excel
1 -
Excel dynamically merge
1 -
Excel Macro
1 -
Excel Users
1 -
Explorer
2 -
Expression
1,716 -
extract data
1 -
Feature Request
1 -
Filter
1 -
filter join
1 -
Financial Services
1 -
Foodie
2 -
Formula
2 -
formula or filter
1 -
Formula Tool
4 -
Formulas
2 -
Fun
5 -
Fuzzy Match
629 -
Fuzzy Matching
1 -
Gallery
605 -
General
93 -
General Suggestion
1 -
Generate Row and Multi-Row Formulas
1 -
Generate Rows
1 -
Getting Started
1 -
Google Analytics
142 -
grouping
1 -
Guidelines
11 -
Hello Everyone !
2 -
Help
4,198 -
How do I colour fields in a row based on a value in another column
1 -
How-To
1 -
Hub 20.4
2 -
I am new to Alteryx.
1 -
identifier
1 -
In Database
868 -
In-Database
1 -
Input
3,783 -
Input data
2 -
Inserting New Rows
1 -
Install
3 -
Installation
311 -
Interface
2 -
Interface Tools
1,674 -
Introduction
5 -
Iterative Macro
962 -
Jira connector
1 -
Join
1,773 -
knowledge base
1 -
Licenses
1 -
Licensing
212 -
List Runner
1 -
Loaders
12 -
Loaders SDK
1 -
Location Optimizer
54 -
Lookup
1 -
Machine Learning
233 -
Macro
2 -
Macros
2,539 -
Mapping
1 -
Marketo
12 -
Marketplace
6 -
matching
1 -
Merging
1 -
MongoDB
68 -
Multiple variable creation
1 -
MultiRowFormula
1 -
Need assistance
1 -
need help :How find a specific string in the all the column of excel and return that clmn
1 -
Need help on Formula Tool
1 -
network
1 -
News
1 -
None of your Business
1 -
Numeric values not appearing
1 -
ODBC
1 -
Off-Topic
14 -
Office of Finance
1 -
Oil & Gas
1 -
Optimization
662 -
Output
4,611 -
Output Data
1 -
package
1 -
Parse
2,130 -
Pattern Matching
1 -
People Person
6 -
percentiles
1 -
Power BI
199 -
practice exercises
1 -
Predictive
2 -
Predictive Analysis
832 -
Predictive Analytics
1 -
Preparation
4,708 -
Prescriptive Analytics
188 -
Publish
232 -
Publishing
2 -
Python
742 -
Qlik
36 -
quartiles
1 -
query editor
1 -
Question
18 -
Questions
1 -
R Tool
457 -
refresh issue
1 -
RegEx
2,136 -
Remove column
1 -
Reporting
2,157 -
Resource
15 -
RestAPI
1 -
Role Management
3 -
Run Command
506 -
Run Workflows
10 -
Runtime
1 -
Salesforce
250 -
Sampling
1 -
Schedule Workflows
3 -
Scheduler
377 -
Scientist
1 -
Search
3 -
Search Feedback
20 -
Server
536 -
Settings
768 -
Setup & Configuration
47 -
Sharepoint
483 -
Sharing
2 -
Sharing & Reuse
1 -
Snowflake
1 -
Spatial
1 -
Spatial Analysis
564 -
Student
9 -
Styling Issue
1 -
Subtotal
1 -
System Administration
1 -
Tableau
473 -
Tables
1 -
Technology
1 -
Text Mining
423 -
Thumbnail
1 -
Thursday Thought
10 -
Time Series
401 -
Time Series Forecasting
1 -
Tips and Tricks
3,848 -
Tool Improvement
1 -
Topic of Interest
41 -
Transformation
3,296 -
Transforming
3 -
Transpose
1 -
Truncating number from a string
1 -
Twitter
24 -
Udacity
85 -
Unique
2 -
Unsure on approach
1 -
Update
1 -
Updates
2 -
Upgrades
1 -
URL
1 -
Use Cases
1 -
User Interface
21 -
User Management
4 -
Video
2 -
VideoID
1 -
Vlookup
1 -
Weekly Challenge
1 -
Weibull Distribution Weibull.Dist
1 -
Word count
1 -
Workflow
8,641 -
Workflows
1 -
YearFrac
1 -
YouTube
1 -
YTD and QTD
1
- « Previous
- Next »