Alteryx Designer Desktop Discussions
Find answers, ask questions, and share expertise about Alteryx Designer Desktop and Intelligence Suite.- Community
- :
- Community
- :
- Participate
- :
- Discussions
- :
- Designer Desktop
- :
- PGP Decryption
PGP Decryption
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify Moderator
Hi, we're doing a proof-of-concept for Alteryx, and the very first task is to decrypt a PGP encrypted file pulled from an SFTP server.
I did a forum search and this topic hasn't been discussed for almost 2 years, so I am "hoping" that maybe some new feature has been added that makes this possible.
If it can't be done natively, does anyone have any suggestions?
- Labels:
-
Developer Tools
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify Moderator
I am an encryption novice, but it appears there are several command line options to decrypt PGP. I would call those (via batch file) with the command line tool in alteryx.
1. cli https://support.symantec.com/en_US/article.TECH211002.html (I can't tell if this is their product or just a how to) It is $6000
2. run batch file https://community.alteryx.com/t5/Alteryx-Designer-Discussions/Run-a-batch-file-from-Run-Command-tool...
EDIT:
New proposal is to use python in the python tool. https://pypi.org/project/py-pgp/
Again, I don't really know much about decryption. But python tool and command line (which can run batch, python, C, Fortran, blah blah blah) are the best options for situations where there isn't a native solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify Moderator
Hi Will
Thanks for that. Yes, my research thus far indicated that either a command line or Python approach would be best.
I am hopeful of making Alteryx the default data handling platform within our organisation (currently using an array of tools, including Jitterbit, SSIS and naked code).
Obviously there are many more tasks required other than PGP decryption, so I will find a way to convince my organisation that this particular requirement is a minor issue. If we install PGP on the Alteryx server then I should be able to handle decryption no problem.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify Moderator
Hi @Manning_Oz
I have the same challenge, can you please let me know if you found a solution?
Many thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify Moderator
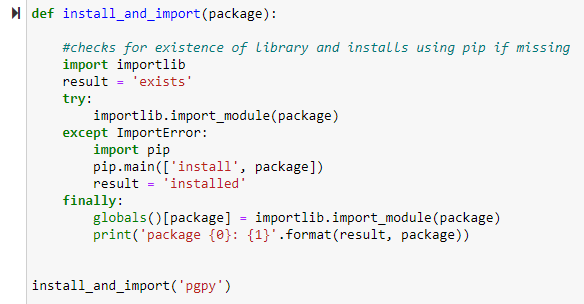
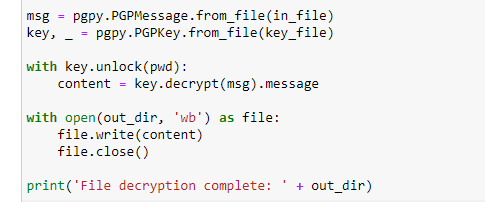
By far the simplest method for this if you are using a PGP key / password is using the pgpy library which is based on the same tech as GnuPG but doesn't require any gpg install.
Pgpy won't be installed in alteryx so you need to run the function below from the python tool to set it up.
Then load file / key to decrypt, job done.. that simple
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify Moderator
thank you for providing this. Please can you elaborate on how to download tool should be configured to work with this. Ive tried doing output to file location with pgp and asc suffixes to later be used as the in_file argument with no success. Should it be outputted as a blob instead? thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify Moderator
@Rhys_Cooper-> if you are retrieving a PGP encrypted file -> you would need to save it as a temp file - or save it as a blob via the download tool. If you save to a specific path you can use that path in python to unencrypt. If you save to a temp file in your download - you will need to capture that location and pass it into your python tool. If you are receiving encoded text - and not a file in your download tool - you would be able to send in just text. Does that make sense?
The short is - the code above expects a file. not a blob.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify Moderator
Hi @apathetichell. Thank you for your responce, it is greatly appreciated. Im currently trying a save to a specific path route which im passing into the python tool ( for posterity, this was using the alteryx read method to read the specified input connection as a dataframe and isolate the specific path using pandas .iloc method on the field) and the using that as the 'in_file' argument.
Its returning "expected ASCII armoureded pgp". ive tried this with reading it as a blob too and have confirmed the sent file is ASCII armoureded pgp. Ive tried manually putting the file format extension in when specifying the save path route (ie .pgp, asc) to no avail.
Any further suggestions would be greatly appreciated!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Notify Moderator
My recommendation here would be to test your code in VSC locally -> using a known encrypted file on your local. Once this is working - migrate to Alteryx. This looks like a syntax issue in your PGP/Python code. Can you confirm you are using Python specific paths (your .iloc is fine you should be using it to extract the path from your Alteryx workflow) -> you may need to make sure that your paths are in c:/.../... format vs c:\...\... format -> not sure if that would lead to this issue but it could.
-
Academy
6 -
ADAPT
2 -
Adobe
204 -
Advent of Code
3 -
Alias Manager
78 -
Alteryx Copilot
26 -
Alteryx Designer
7 -
Alteryx Editions
95 -
Alteryx Practice
20 -
Amazon S3
149 -
AMP Engine
252 -
Announcement
1 -
API
1,210 -
App Builder
116 -
Apps
1,360 -
Assets | Wealth Management
1 -
Basic Creator
15 -
Batch Macro
1,559 -
Behavior Analysis
246 -
Best Practices
2,696 -
Bug
720 -
Bugs & Issues
1 -
Calgary
67 -
CASS
53 -
Chained App
268 -
Common Use Cases
3,825 -
Community
26 -
Computer Vision
86 -
Connectors
1,426 -
Conversation Starter
3 -
COVID-19
1 -
Custom Formula Function
1 -
Custom Tools
1,939 -
Data
1 -
Data Challenge
10 -
Data Investigation
3,489 -
Data Science
3 -
Database Connection
2,221 -
Datasets
5,223 -
Date Time
3,229 -
Demographic Analysis
186 -
Designer Cloud
743 -
Developer
4,376 -
Developer Tools
3,534 -
Documentation
528 -
Download
1,038 -
Dynamic Processing
2,941 -
Email
929 -
Engine
145 -
Enterprise (Edition)
1 -
Error Message
2,262 -
Events
198 -
Expression
1,868 -
Financial Services
1 -
Full Creator
2 -
Fun
2 -
Fuzzy Match
714 -
Gallery
666 -
GenAI Tools
3 -
General
2 -
Google Analytics
155 -
Help
4,711 -
In Database
966 -
Input
4,296 -
Installation
361 -
Interface Tools
1,902 -
Iterative Macro
1,095 -
Join
1,960 -
Licensing
252 -
Location Optimizer
60 -
Machine Learning
260 -
Macros
2,866 -
Marketo
12 -
Marketplace
23 -
MongoDB
82 -
Off-Topic
5 -
Optimization
751 -
Output
5,259 -
Parse
2,328 -
Power BI
228 -
Predictive Analysis
937 -
Preparation
5,171 -
Prescriptive Analytics
206 -
Professional (Edition)
4 -
Publish
257 -
Python
855 -
Qlik
39 -
Question
1 -
Questions
2 -
R Tool
476 -
Regex
2,339 -
Reporting
2,434 -
Resource
1 -
Run Command
576 -
Salesforce
277 -
Scheduler
411 -
Search Feedback
3 -
Server
631 -
Settings
936 -
Setup & Configuration
3 -
Sharepoint
628 -
Spatial Analysis
599 -
Starter (Edition)
1 -
Tableau
512 -
Tax & Audit
1 -
Text Mining
468 -
Thursday Thought
4 -
Time Series
432 -
Tips and Tricks
4,187 -
Topic of Interest
1,126 -
Transformation
3,732 -
Twitter
23 -
Udacity
84 -
Updates
1 -
Viewer
3 -
Workflow
9,983
- « Previous
- Next »