Alteryx Server Knowledge Base
Definitive answers from Server experts.Configuring SAML on Alteryx Server for ADFS
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Notify Moderator
08-16-2019 09:40 AM - edited 07-23-2021 03:56 PM
Configuring SAML on Alteryx Server for Active Directory Federation Services (ADFS)
Alteryx Server has the ability to use most identity providers that support the SAML 2.0 standard, and from my testing, ADFS is no exception! The following information will assist with configuring Alteryx Server to be functional with ADFS.
Please note the following information is based on third-party software and processes may be slightly different on older or newer versions of the software. The following was created against ADFS v4.0 running on Windows Server 2016 and Alteryx Server 2019.2.
Prerequisites
- AD FS Server
- Account with access to perform administration tasks
- All users that will login must have an email address attribute
- Alteryx Server >= 2018.2
- Account with access to perform administration tasks
- SSL/TLS Certificate Installed on Alteryx Server (Self-Signed certificate is not recommended)
Procedure
- Verify that your Alteryx Server's Gallery function has been configured with SSL/TLS enabled on each Gallery node in the environment and that a proper SSL certificate is installed. Instructions are provided in the link above.
- This and following steps will require an ADFS administrator. Open the AD FD Management utility (Start > Windows Administrative Tools > AD FS Management)
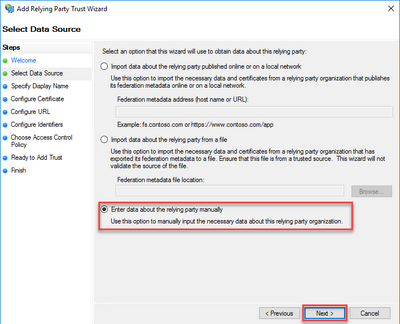
- ClickRelying Party Trusts from the console, then clickAdd Relying Party Trust...
- ClickEnter data about the relying party manually and clickNext.
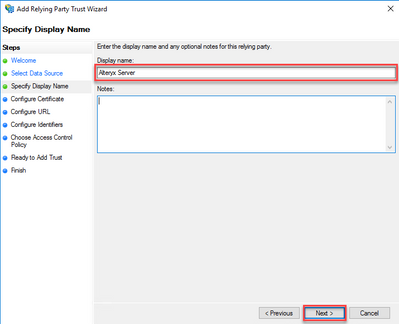
- Type aDisplay name for the trust. I placed "Alteryx Server" here, but you can use a name that best identifies the connection for you, such as a server name or other easily identifiable name. Then clickNext.
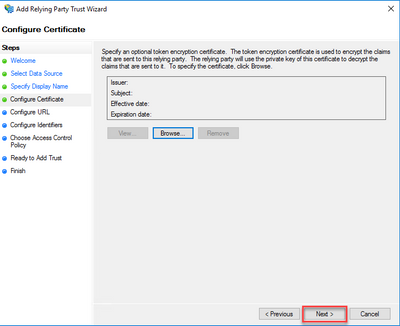
- ClickNext on theConfigure Certificate page.
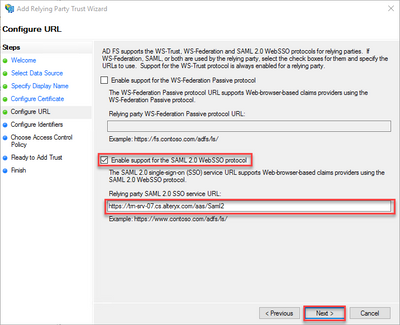
- Check the box forEnable support for the SAML 2.0 WebSSO protocol. Type the URL of the Alteryx Server's SAML endpoint in the Relying party SAML 2.0 SSO service URL box, which typically will be the base URL of Alteryx Gallery with the addition of "/aas/Saml2". Once you have added the proper URL, clickNext.
Note:this endpoint may be case sensitive depending on settings in your environment. I would recommend entering it with the capitalization as shown in the screenshot and example below.
Example:
Gallery URL: https://trn-srv-07.cs.alteryx.com/gallery
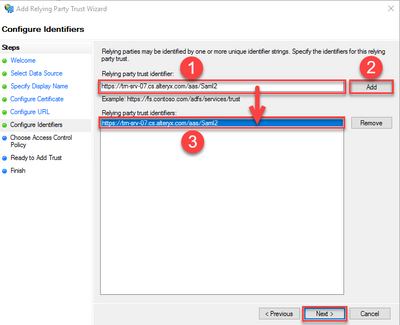
SAML Endpoint: https://trn-srv-07.cs.alteryx.com/aas/Saml2 - In theRelying party trust identifier, type the same SAML endpoint as the previous step and clickAdd to add the URL to the list below. ClickNext.
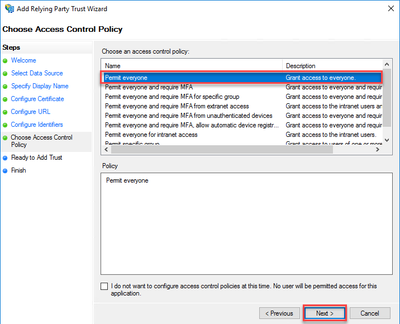
- SelectPermit everyone from the Access Control Policy and click Next.
Note: You may wish to configure this option differently depending on the environment and whom you wish to be able to authenticate with Alteryx Gallery, or you may wish to setup Multi-Factor Authentication (MFA). Specific access permissions and these types of setup are outside the scope of this article. - ClickNext on theReady to Add Trust page.
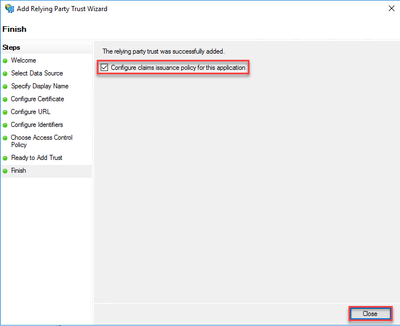
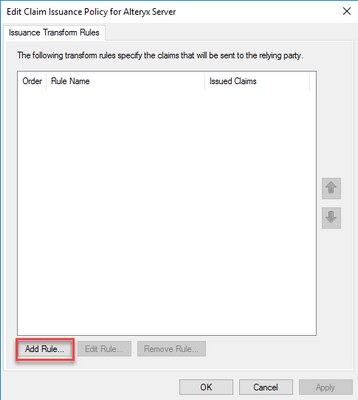
- Check the box next toConfigure claims issuance policy for this application and clickClose.
- Within the new Claim Issuance Policy window, clickAdd Rule...
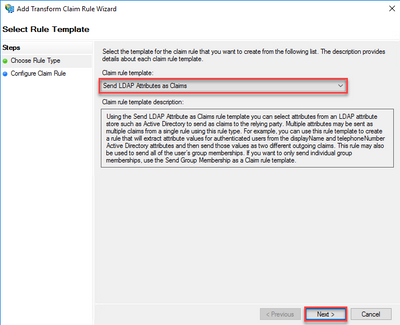
- Verify theClaim rule template is set toSend LDAP Attributes as Claims and clickNext.
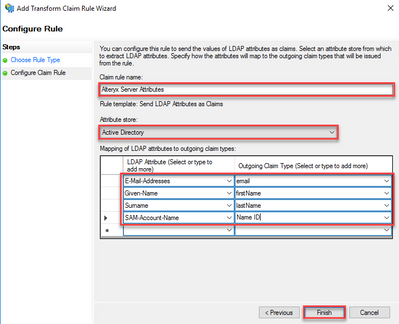
- Type a desired name for the rule within theClaim rule name box. From theAttribute store drop-down, chooseActive Directory.
- Using the following table, set the appropriate options within theMapping of LDAP attributes to outgoing claim types box. ClickFinish.
Note: The following outgoing values are case sensitive and will need to be typed except for "SAM-Account-Name".
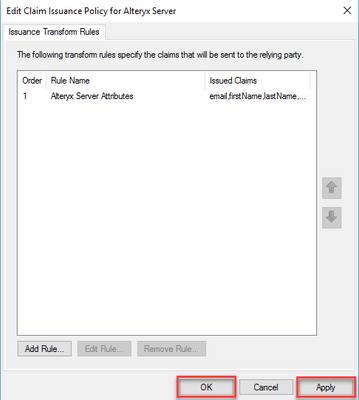
LDAP Attribute Outgoing Claim Type E-Mail-Addresses email Given-Name firstName Surname lastName SAM-Account-Name Name ID - On the Claim Issuance Policy window, clickApply to apply the settings, then clickOK.
- You will now need an administrator with access to the Alteryx Server machine(s) running the Gallery for your environment. Connect to the machine remotely via Remote Desktop.
- Open theAlteryx System Settings application, then clickNext until you are at theGallery > Authentication page.
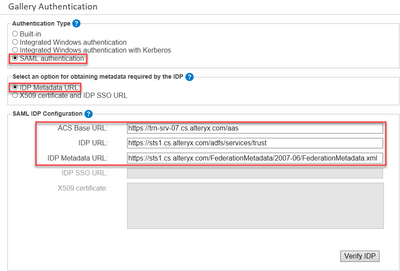
- From theAuthentication Type box, click the radio button next toSAML authentication. In theSelect an option for obtaining metadata required by the IDP, click the radio button next toIDP Metadata URL.
!Warning!: It is not recommended to change the authentication type once you have established the persistence layer (e.g. MongoDB) and started using a particular authentication method in your environment. Differences in user account structure will be likely to result in errors in the Gallery if the authentication method is changed in an established environment. If you are changing authentication methods, it is recommended to create a new persistence database! - From the SAML IDP Configuration box, set theACS Base URL to the root of the Gallery URL plus "/aas".
Example:
Gallery URL: https://trn-srv-07.cs.alteryx.com/gallery
ACS Base URL: https://trn-srv-07.cs.alteryx.com/aas - Set theIDP URL(also known as Entity ID)to theFederation Service identifiervalue from ADFS.
Example: https://sts1.cs.alteryx.com/adfs/services/trust
Note: If you are not positive on the value for this, ask your ADFS administrator or download the metadata XML with the link you are using in the next step and look for the "entityID". - SettheIDP Metadata URL to the location of the Federation Metadataxml file provided by the ADFS server.
Example:https://sts1.cs.alteryx.com/FederationMetadata/2007-06/FederationMetadata.xml
Note: If you are not positive on the value for this, ask your ADFS administrator. - ClickVerify IDP. If all goes well, you should receive a message similar to the following:
Note: See theCommon Issues section below for tips on troubleshooting! - ClickNext through the remainder of the System Settings dialogs, then clickFinish.
- (Optional) Return to Step 17 if you have additional Gallery node(s) to configure.
- Once all Gallery node(s) are configured, attempt to access your private Alteryx Gallery and log in with your fresh new SAML configuration!
Common Issues
-Turn offIE Enhanced Security Configuration on the Alteryx Server if you have crash errors while verifying the IDP information. This feature can be turned back on once you have the configuration in a functional state.https://www.limestonenetworks.com/support/knowledge-center/17/70/how_do_i_disable_internet_explorer_...
-Verify that the values in theSAML IDP Configuration are correct for your ADFS server.
-Verify that the ADFS server was configured with the correct claim attributes.
-Check the AlteryxAuthorizatonService.exe logging directory (%PROGRAMDATA%\Alteryx\Logs) for any clues.
-OpenEvent Viewer within Windows and look for errors that may be of use in theApplication log.
-If still stuck, reach out to our Support team. I'd suggest providing the following:
1. Values set in the Alteryx System Settings application for SAML
2. AAS log files (found in %PROGRAMDATA%\Alteryx\Logs\)
3. Configuration screenshots for ADFS
Additional Resources
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Notify Moderator
@MikeSp at it again... being the smartest guy I know.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Notify Moderator
Just in time! Mike
-
11.0
1 -
2018.3
11 -
2019.3
12 -
2019.4
13 -
2020.4
19 -
2021.1
19 -
2021.2
24 -
2021.3
19 -
2021.4
25 -
2022.1
21 -
Alteryx Gallery
3 -
Alteryx Server
7 -
Apps
16 -
Best Practices
37 -
Chained App
4 -
Collections
7 -
Common Use Cases
35 -
Customer Support Team
2 -
Database Connection
30 -
Datasets
4 -
Documentation
1 -
Dynamic Processing
4 -
Error Message
79 -
FIPS Server
2 -
Gallery
193 -
Gallery Administration
31 -
Gallery API
9 -
How To
95 -
Input
13 -
Installation
31 -
Licensing
13 -
Logs
7 -
Macros
8 -
MongoDB
57 -
Output
11 -
Permissions
5 -
Publish
25 -
Reporting
10 -
Run Command
6 -
SAML
9 -
Scheduler
45 -
Settings
52 -
Support
1 -
Tips and Tricks
50 -
Troubleshooting
6 -
Updates
8 -
Upgrades
18 -
Use Case
1 -
Windows Authentication
13 -
Workflow
35
- « Previous
- Next »